It seems like a lot has been said about the importance of robust security in healthcare. Yet time and again security breaches continue to grab headlines as healthcare providers and software developers are falling into avoidable security pitfalls.
Between 2009 and 2022, the HHS Office for Civil Rights reported 5,150 data breaches. As a result of those breaches, over 382 million healthcare records were exposed. What’s more, the average cost of a healthcare breach has increased by 29.5%, amounting to $9.3 million per incident.
Healthcare data breach statistics

Source: Compliancy-group
In the digitized world of healthcare, robust security isn’t just a requirement — it’s a necessity. Cybersecurity mistakes can impede a healthcare organization’s ability to provide high-quality care and compromise patient trust. These threats can come from a variety of internal and external sources.
Medical data breach types by year (2021 to June 2022)

Source: Freeagent
In this article, we are going to shine the light on the ten most common security mistakes in healthcare software development to help providers and software engineers stay on top of potential threats. As they say, informed means armed.
Mistake #1: Inadequate access controls
The gatekeeper to your healthcare solution, access controls determine who has the ability to view and manipulate the data within the system. Thus, insufficient or poorly implemented access control can result in unnecessary privileges being granted to users, exposing sensitive information to potential theft.
To limit access within a healthcare solution, a role-based access control model is often used. This method ensures that only those with proper authorization can access the solution, depending on their designated role. Let’s consider an example — a doctor requires access to a patient’s complete medical records, while administrative personnel might only need billing and contact details.
For a more rigorous defense, pair role-based access control with MFA, or multi-factor authentication. MFA demands users to confirm their identity using a minimum of two validation methods before gaining access. Progressive healthcare providers are increasingly adopting biometrics-based authentication, which uses distinct characteristics such as facial features, voice, or fingerprints for user identification. This type of authentication proves particularly effective in warding off a variety of common attacks, including those from insiders and threats to identity privacy.
Mistake #2: Not encrypting sensitive data
The lack of data encryption is another dangerous mistake that can cause an unexpected data breach. A striking example of this occurred back in 2013 when Advocate Health Care experienced a significant data violation. The breach was not the result of some sophisticated cyber-attack. It was simply due to the fact that four personal computers with unencrypted medical information were stolen. Consequently, this led to the exposure of data about 4 million patients.
Robust encryption of sensitive patient data is a must in order to protect patients’ privacy and confidentiality. There are two key stages where data encryption is essential — at rest and in transit. Data at rest is used for information stored on physical or virtual data centers, databases, or personal devices, while data in transit describes information moving through networks. It’s important to encrypt data using strong and up-to-date encryption methods like AES, DES, Blowfish, RSA, and more. Using secure communication protocols like HTTPS and TLS can help protect data as it moves between systems.
Mistake #3. Vulnerable APIs
As healthcare moves to the era of interoperability and seamless health data exchange, API adoption is rapidly increasing — but so do cybersecurity risks. If not properly secured, APIs can often become the weakest link in the security chain, providing an express lane for attackers straight to healthcare data. Bad actors can use vulnerable APIs in a variety of ways as shown below.
Application and API attack patterns

Source: TechTarget
Securing APIs requires a comprehensive approach. It encompasses the implementation of robust authentication and authorization mechanisms like OAuth 2.0. In addition, APIs should validate and sanitize all input data to prevent attacks such as SQL injections. Rate limiting is another useful tool, as it restricts how often a user or IP address can call your API in a given timeframe, reducing the risk of DDoS attacks or brute-force login attempts.
Mistake # 4. Over-reliance on third-party components
From specific libraries and frameworks to existing tools and modules, third-party components are often incorporated into software solutions to accelerate the pace of development. But the assumption that those components are innately secure can be rather dangerous. While offering numerous benefits, third-party systems can also introduce vulnerabilities that can often go unnoticed until they are exploited by a malicious party, causing potentially irreparable damage.
But how can you avoid falling into this trap? Before integrating a new component, review its security documentation and known vulnerabilities, and analyze how it handles sensitive data. It can be a good idea to use specialized software composition analysis tools as they can automatically detect your software’s third-party components and identify any known vulnerabilities.
Mistake #5. Security misconfigurations
In 2018, St. Louis-based BJC Healthcare, a non-profit healthcare conglomerate, announced that a data leak affected over 33,000 patients. The cause was a misconfigured server that left confidential information easily accessible for more than 8 months.
Misconfigurations can open a security flaw even in the most rock-solid solutions. They can occur in many areas: firewalls, server settings, cloud storage settings, database access controls, encryption settings, and more.
Common types of security misconfigurations

Source: Brightsec
To avoid misconfigurations, it’s important to have a clear understanding of all data flows and configuration settings in the solution. The production, dev, and test environments must be configured in the same way but with distinct passwords in order to easily establish a secure environment. Regular auditing and automated configuration management tools can also help identify potential misconfigurations.
Mistake #6: Neglecting data backups
In the event of a cyberattack like ransomware, where an attacker encrypts data and demands a ransom for its release, a recent backup can be a lifesaver. It allows you to restore the system to its pre-attack state without capitulating to the attackers’ demands. But without regular data backups, you could find yourself in a position of having to negotiate with cybercriminals or lose your data entirely.
Hence, it’s critical to implement and maintain a regular schedule for backing up your healthcare software. The regularity of these backups can vary depending on the rate at which your data alters. In an environment where data changes are frequent, daily or even hourly backups might be needed. In addition, remember to test your backups periodically to confirm that the data can be effectively restored if required.
Mistake #7: Ignoring regular updates and patch management
Another common mistake in healthcare software development is failing to implement security updates and patches in a timely manner. Attackers continuously evolve their tactics and find new loopholes and leaks in software solutions to exploit. The latest survey from the Ponemon Institute showed the following:
- 60% of breach incidents occurred due to a known vulnerability that remained unpatched, even though a patch is available;
- 62% of organizations were unaware that they were vulnerable before the data breach;
- 48% of businesses report that they have experienced a data breach during the last couple of years.
Patches and updates are the first line of defense against known vulnerabilities. A comprehensive update and patch management strategy includes keeping track of patches and updates for the components of your healthcare solution and prioritizing them based on the vulnerabilities they fix. Automated patch management can help accelerate this process and make it smoother.
Mistake #8: Insecure design
Another critical yet often overlooked aspect of developing a secure healthcare solution is the system’s design. To illustrate this idea, suppose a user wants to change the password. If the form dispatches a GET request rather than a POST, the user’s data, including the old and new passwords, will be displayed in the URL bar. In this case, anyone using the same computer could potentially see this sensitive data in the browser history.
https://example.com/app/changePassword?oldPassword=hunter2&newPassword=hunter3
This is a classic example of insecure design, demonstrating that sensitive details should only be transmitted via secure methods and never be stored in plaintext.
Mistake #9: Poor error handling
Running out of memory, database inaccessibility, system call failure, network timeout, and more — a hundred of common conditions can cause an error in your healthcare solution. If not properly handled, these errors can become a cause of security problems. For instance, detailed error messages like database dumps and stack traces can give attackers useful information about the system implementation that should never be revealed.
Server error message example
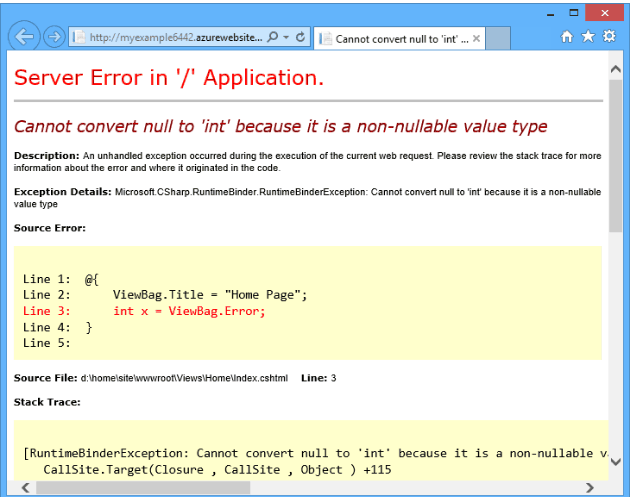
Source: Astra
Therefore, a well-thought-out strategy is needed for error and exception handling in order to provide useful information to users, meaningful insights to IT support, and no information to attackers.
Mistake #10: Inadequate logging and monitoring
The backbone of a proactive security approach, logging and monitoring provide visibility and help identify abnormalities or suspicious patterns that could indicate a security incident. Without comprehensive logging, it could take weeks or even months to detect a breach, providing attackers enough time to exploit the system and steal sensitive data.
To avoid this mistake, make sure to collect and manage logs from all components of the solution, set up automated alerts for suspicious activities, and regularly review and analyze these logs for signs of potential security threats. In addition, consider incorporating advanced solutions like Security Information and Event Management (SIEM) tools or employing machine learning algorithms to detect anomalies in data patterns. These tools can aid in streamlining the log analysis and increase the chances of catching a security incident early.
The bottom line
As our reliance on technology in healthcare deepens, so does the importance of robust security measures. Whether it’s the failure to adequately control access, ignoring the necessity of regular updates and patches, neglecting data backups, or mismanaging error handling, each security mistake holds the potential to expose sensitive patient information. And with the sky-high cost of an average healthcare breach, the price of overlooking these pitfalls is too high to afford.