Few other industries are so heavily regulated as healthcare. Setting the standard for high-quality care, safeguarding sensitive patient data, preventing fraud and abuse — it all requires a set of robust rules, laws, and regulations mandatory for all participants of the healthcare domain.
One of such key regulations is HIPAA, or Health Insurance Portability and Accountability Act. Designed to ensure health data privacy and security, HIPAA applies to all healthcare software solutions and applications that handle patient information. And penalties for HIPAA non-compliance are hefty, reaching up to $50,000 per individual violation or $1.5 million per calendar year for HIPAA violations.
Building a HIPAA-compliant healthcare solution is no easy endeavor as a lot needs to be taken into consideration. But before we move to the essential components of any HIPAA-compliant app, let’s start with HIPAA basics.
Understanding HIPAA
Adopted in 1996, this crucial piece of legislation represents a significant shift in the way we approach healthcare data. HIPAA aims to provide patients with better control over their medical information, ensure health data privacy and accessibility, and protect health insurance coverage. For that, HIPAA prescribes a number of rules:
- Privacy Rule addresses the use of protected health information (PHI) with the purpose to ensure its safety and a free flow needed to promote high-quality care.
- Security Rule establishes technical and non-technical safeguards to ensure the protection of PHI defined in the Privacy Rule.
- Enforcement Rule describes the procedures for conducting investigations, hearings, as well as penalties for HIPAA violations.
- Breach Notification Rule requires covered entities to timely notify patients if their health data is breached.
Is your healthcare software solution subject to HIPAA?
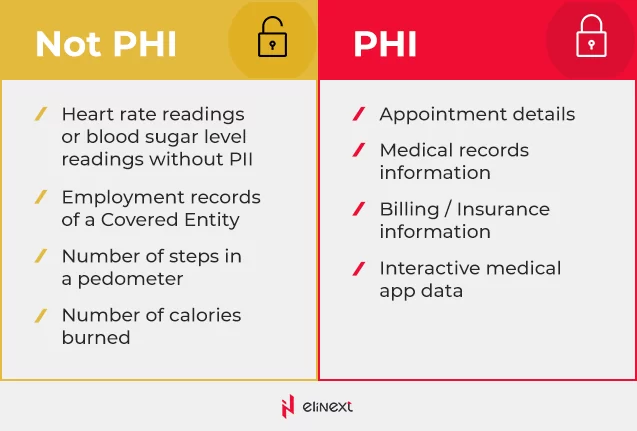
As it is clearly seen from HIPAA rules, any healthcare application that stores, processes, or transfers PHI in an electronic form (ePHI) must comply with HIPAA regulations. To that end, PHI includes all personally identifiable information like names, addresses, social security numbers, biometrics identifiers, medical record numbers, and more. However, the number of steps or heart rate readings transmitted by a medical wearable are not considered ePHI.
Eligraphics below demonstrates key types of PHI and non-PHI data.
If you design a healthcare solution that will be regulated by HIPAA, it is important to implement key technical safeguards prescribed by HIPAA Security Rule in order to protect patients’ PHI and take data safety worries out of the equation.
Making your healthcare app HIPAA-compliant
From permission-based access control to multi-factor authentication to HIPAA-compliant cloud storage, a lot goes into ensuring robust and reliable protection of health data. The graphics below shows five main standards that HIPAA Security Rule is predicated on.
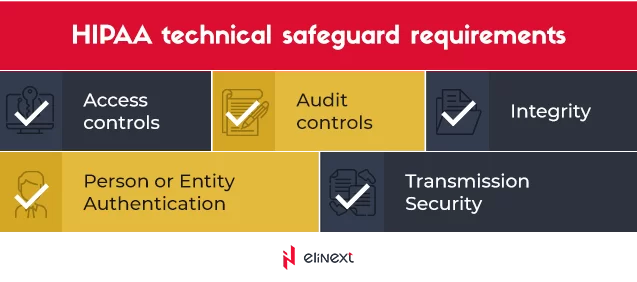
Access controls
While controlling access to an application and information within seems like an obvious measure, the amount of data stolen because of poor access control is overwhelming. The notorious Anthem data breach left some 80 million medical records exposed and the authorities believe that it was the lack of proper access control that allowed hackers to breach patient data. Now, the US health insurer is to pay almost 40 million — a pricey lesson for anyone.
Here’s what you can do to ensure that only authorized persons with respective access rights have access to ePHI:
- Implement role-based access control (RBAC) to assign granular permissions, rights, and privileges
- Use a unique user identifier to track user activity when they are logged into the system
- Set up automatic log-off to prevent unauthorized access to sensitive data
Audit controls
Anything related to security must be regularly audited. A HIPAA-compliant healthcare solution must be able to generate detailed audit logs in order to ensure visibility into a system and help a healthcare provider stay on top of any suspicious activity.
Generally, audit logs can include the following information:
- Changed passwords
- Successful and failed logins
- New added users
- Firewall logs, and more
Integrity
Hacking incidents have demonstrated that health data integrity can easily be compromised. What’s more, data integrity can be corrupted even on its own through system glitches or errors when saving a file. That said, any unintentional or accidental changes to ePHI can result not only in poor quality of care but also in patient safety issues. That’s why it is crucially important to protect ePHI against unauthorized alteration or destruction.
Data corroboration features that you can implement in a healthcare solution include:
- Checksum verification
- Digital signatures
- Double-keying
Person or entity authentication
According to recent research, around 80% of data breaches are caused by weak or compromised credentials. Strong authentication can be the first line of defense protecting your healthcare solution from hackers and ensuring safety of end users’ health data.
Essentially, authentication means that users are who they claim to be, and there are different ways to provide proof of identity:
- Something a user knows like a password or a PIN
- Something a user possess like a token or a key
- Something unique to a user like biometrics (fingerprints, iris, facial structure, voice patterns)
The best practices include the use of multi-factor authentication that leverages two and more forms of identification for an extra layer of security.
Transmission security
As data travels to and from your healthcare application, it becomes particularly vulnerable and exposed to many risks. Unsecure networks can make it easy for cybercriminals to interfere and steal data with no need to hack the solution itself.
To ensure that all communication over a network is secure, the following measures can be applied:
- End-to-end encryption (E2EE) of data in transit and at rest
- Secure communication protocols (TLS or SSL)
- Data or message authentication code
Undoubtedly, all healthcare applications are different and require a unique approach towards compliance. For example, if you are building a cloud-first solution, you also need to leverage HIPAA-compliant cloud storage. In this healthcare case study, you can read more about a patient portal that utilizes AWS cloud infrastructure to ensure scalability and high availability while meeting HIPAA requirements.
Key takeaways
While HIPAA adds complexity to the already tricky regulatory framework, non-compliance is not an option. HIPAA is one of the most important pieces of healthcare legislation that aims to protect patients from theft and fraud while giving them greater control over their health data. To that end, HIPAA prescribes technical safeguards that must be implemented in all healthcare solutions dealing with PHI.