The objective of this article is to show how we can build a secure application for providing financial operations.
First, we start with architecture development.
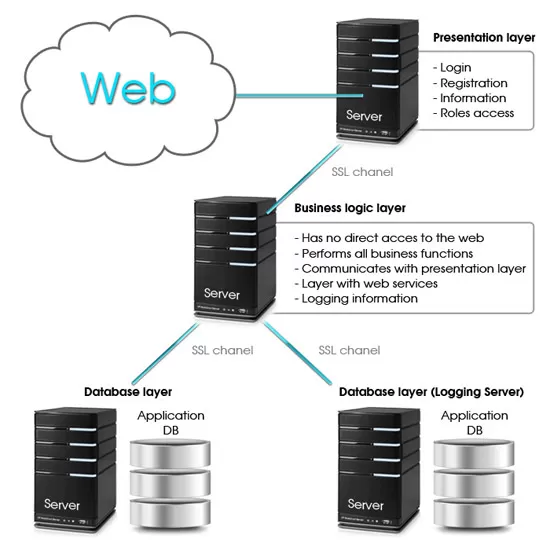
To make our application secure, we can use a three-layer architecture. It means that we split our application into three layers: database layer, business logic layer, and presentation layer. These layers are illustrated in Figure 1:
Why doing this? From the image we can see that only the presentation layer is available from the web, so we minimize risks that our application will be broken by hackers because the business logic layer has no access to the web. We can also improve this scheme by adding IP restriction for incoming requests on BL Server. Communicating with the presentation layer by using web services also enables us to make our presentation independent from the platform, and in future, we will be able to add easily, for example, a mobile agent that will use the existing web services for work. Separate DB was also used for the previous aims, and we can as well add IP restriction. So, if you implement this scheme, you will do a great job to improve the security of your application.
Next step for improving security with SSL.
By default, all requests use HTTP protocol, which is not secure. All traffic is sent by HTTP as a clear text, so anyone can “listen” to your server and collect all the necessary information. To prevent this, we use SSL that encrypts the channel between the browser and the server. When you configure IIS, you can notice several settings for SSL:
- Ignore client certificate;
- Accept client certificate;
- Require client certificate.
When you use the “Ignore client certificate” setting, your channel will be secure, but anyone can send a request to the server. This mechanism is useful for login forms and other forms where users send secure information. If you choose to accept certificates, your server will ask for a certificate but will not necessarily deny access if the certificate is not provided. If you select “Require client certificates”, the user must supply a valid certificate or the user will receive an error message. By selecting the “Require” option we cover two security issues: only users with a valid client certificate can access the server, the connection is really encrypted; and you know who works with the server (because you can track logged users and their certificates). We also use this SSL type between our servers to protect channels between our applications.
And the last step is Logging.
You should log all important operations, such as authentication events, login attempt count, all operations for writing/editing the date, reading secure data, server events, etc. If the log system is implemented correctly, it enables us to detect attacks, to diagnose errors, and to recover from attacks. I also suggest the implementation of a mechanism for hashing log entries, which prevents our system from changing logs.
In this article, we have reviewed some mechanisms for designing a secure application. If you use this rules while developing your application, you will certainly increase security.
Industries and Technology Areas:
Industries: finance, banking, investment management, asset management
Technology Areas: software development, ASP.NET, SSL, three-layer architecture, HTTPS