Protecting data in software projects means implementing technical, legal, and process controls (access restrictions, encryption, auditing, secure hosting, backups, incident response) to ensure that information remains confidential, secure, and accessible from development through long-term support.
Companies using custom software development services include startups processing user data, small and medium-sized businesses moving to the cloud, large companies needing to comply with regulations (GDPR/HIPAA/PCI), and any teams sharing intellectual property, credentials, or customer records with suppliers.
Data protection during development is paramount, with statistics for 2026 showing that 60% of data breaches are due to insufficient controls. Data analytics services automate access monitoring, encryption, and anomaly detection. Impact: The average cost of a data breach is $4.44 million. Benefits: 75% faster recovery, 30% reduction in incident costs, and compliance with global standards.
Who Is Responsible for Data Breaches?
The most common causes of major cybersecurity violations can be divided into two categories: people and cyber hygiene. The human factor is related to the behavior of employees and how they interact with corporate systems. Cyber hygiene refers to the extent to which companies maintain and update their systems and software.
In 2025, 63% of companies affected by data breaches lacked clearly defined data protection policies and data privacy in software development. For example, the use of shadow AI resulted in additional losses of $670,000 per breach. Responsibility must be shared between data leaders, information security leaders, and developers, all working together.
Attackers often take advantage of people’s carelessness, curiosity, greed, and anxiety. For example, hackers sent out malicious emails about COVID-19-related topics. People received fake emails on behalf of the Centers for Disease Control and Prevention (CDC). They were offered to fill out a summary of recent cases of coronavirus among neighbors. For this purpose, they were asked to follow the link and enter their email login and password. As a result, criminals got their credentials.
Phishing has been and continues to be a huge business problem because employees often open unauthorized emails and install scumware on their computers. That’s why businesses must learn how to respond to the rise in psychological and phishing attacks. Security officers must inform employees who interact with systems and train them to recognize suspicious content and use strong passwords to protect their corporate accounts.
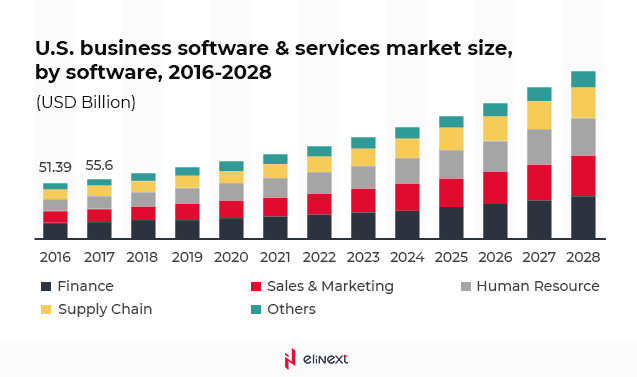
Custom software development companies should especially pay more attention to the protection of their projects. The eligraphics based on the Grand View Research data shows that the global software and services market value stood at almost $390 billion in 2020. It is predicted to grow by 11.3% by 2028.
Seeking to seize big investments and valuable information circulated in this sector, hackers come up with more and more sophisticated ways to break your security barriers. Taking into account the fact that software development companies often cooperate with freelancers and outsourced teams who work from home and use their own devices and networks, it’s vital for their business to protect their projects during and after the development stage.
Prioritize protecting data in software projects to avoid costly breaches and ensure long-term business success.
Be On Guard of Your Confidential Information
There are two ways to protect private information: organizational data security measures and technical data security tools.
Organizational Data Security Measures
Every company (security officer or security department) must develop a set of organizational measures aimed at protecting confidential information. As a rule, it includes the following:
Data protection during development is challenging due to constantly evolving threats and fragmented responsibilities. Mobile app development company Elinext integrates data protection into the development phase, leveraging access control, encryption, and continuous monitoring. This reduces the risk of data leakage, ensures regulatory compliance, and protects the company’s reputation.Elinext Expert Quote
Technical Data Security Tools
The technical data security tools include the following software and hardware:
Security Testing
This testing strategy is aimed at checking software, data, and IT infrastructure for vulnerabilities and determining whether they are protected from hacker attacks. Security testing must be included in the software development life cycle (SDLC) from the first stages. The security testers usually perform the following tests:
- DDoS stress testing;
- Penetration testing;
- Vulnerability testing;
- Standard-compliant testing;
- Risk assessment;
- Ethical hacking;
- Security auditing.
- These measures will allow you to reveal and fix weak points and be armed before the development stage.
Data Encryption
Encryption is the process of converting data into characters that cannot be read without knowing the rule (algorithm) by which they were created. Changing data using the selected algorithm is activated using a special key, which is also a certain set of characters. The longer the key, the more reliable it is. Without the key, the information will be a bunch of meaningless symbols.
In 2025, data encryption used in protecting data in software projects accounted for 23% of all data security threats (DLP). Strong encryption and automated response reduced breach remediation costs by $1.9 million. The adoption of post-quantum cryptography is growing.
Creating Strong Passwords
Each employee or project team member must come up with and use a strong, unique password. It must consist of numbers, characters, symbols, and letters so that hackers can’t crack it. The SafetyDetectives specialists analyzed more than 18 million passwords and revealed that the most predictable and hacked passwords were passwords in the US, 123456 in Germany, and qwerty in Russia. Criminals didn’t even have to try to guess for them.
It’s a very bad idea to use short passwords, too. For example, a computer spends milliseconds to crack a seven-digit password. If you find it difficult to create a reliable, long password, you can always use password managers that will help you protect your data.
Two-Factor Authentication
Two-factor authentication is a user verification method that includes an additional layer of security by requiring not one, but two identity facts at once. For authentication, people usually enter a username and password, which are easy to crack. For example, a login often matches a phone number and email address, while a password is easily guessable by answering security questions. In the case of two-factor authentication, another verification method is used. It can be scanning a fingerprint, identifying the user’s face, etc.
Antivirus Software
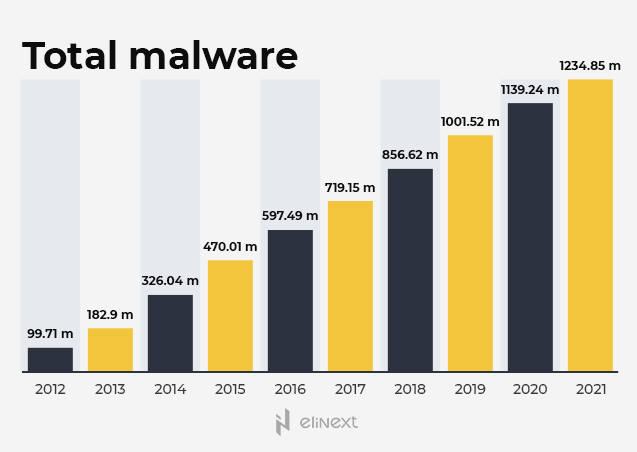
If a virus or malware enters your device, then all the above-mentioned measures will be useless. Hackers exploit viruses to transfer your private data and other confidential information to their servers. When choosing antivirus software, it’s important to pay attention to the ability to automatically update the antivirus databases as new viruses appear every day. AV-Test Institute detects more than 350k new pieces of malware per day. AV-Test Institute detects more than 350k new pieces of malware per day.
Data Loss Prevention Solutions
While working on a project, the team and the customer constantly exchange various documents, files, passwords, logins, and other confidential information. Data Loss Preventions (DLP) solutions analyze incoming and outgoing data for confidentiality. When it is detected, the message transfer is immediately blocked. These instruments are currently gaining popularity.
Protecting data in software projects market is expected to reach $35.38 billion by 2025, with AI-based DLP solutions saving $2.22 million per breach. The financial services (BFSI) sector led the way, accounting for 27% of DLP revenue.
Data Backup and Recovery
Data backup is creating a copy of your files on another device or in the cloud in case the main device is lost or damaged. The appropriate instruments and services will save you thousands of dollars because you won’t have to pay for downtime. How much can your business lose if attackers break your systems?
Data backup and recovery, data privacy in software development are vital, as the average cost of a data breach in 2025 was $4.44 million, and ransomware was $5.08 million per incident. 85% of businesses use automated recovery, reducing downtime by 75%.
Invest in protecting data in software projects to ensure asset safety and build customer trust in the future.
Your Project is Launched: What Comes Next?
Signing a non-disclosure agreement (NDA) with your team will ensure data security after the development of your project. This agreement should define the rules for the transfer, disclosure, return, or destruction of confidential information after the completion of the project. Each party must clearly understand that it is responsible for the disclosure of any data. Of course, the NDA must be signed before starting work on the project. However, it must describe how to handle confidential information when the project is over.
Conclusion
Cybersecurity solutions and data protection during development are now business-critical. By 2025, AI-powered monitoring, automated backups, and strict access controls will be standard. A fintech company using these solutions reduced breach remediation costs by 30% and recovery time by 75%. Companies implementing these trends achieve resilience and regulatory compliance.
FAQ
Why is data protection important during a development project?
Data protection during development is essential to prevent data breaches, ensure compliance, and protect sensitive data. Encryption and access control mitigate risks.
How should sensitive data be handled during development?
Data privacy in software development means encrypting sensitive data, restricting access, and using anonymized test data. For example, masking personal data in test environments.
How can access to data be controlled during the project?
Data protection during development uses role-based access, multi-factor authentication, and regular audits. For example, only authorized developers have access to production data.
What security practices should developers follow?
Protecting data in software projects requires secure coding, code reviews, vulnerability scanning, and regular updates. Example: Static code analysis tools.
How should data be protected when working with third parties?
Data privacy in software development requires contracts, audits, and encryption when exchanging data with third parties. For example, vendor security assessments.
How can we ensure long-term data protection after deployment?
Protecting data in software projects after deployment involves regular updates, monitoring, and backups. An effective solution is automated patch management and immutable backups.