Sensors, robots and cloud technology – here’s how the Internet of Things disrupts the business world with connectivity and automation. The new concept interest a lot of companies, however, few bring the ideas to life, and the main reason is security.
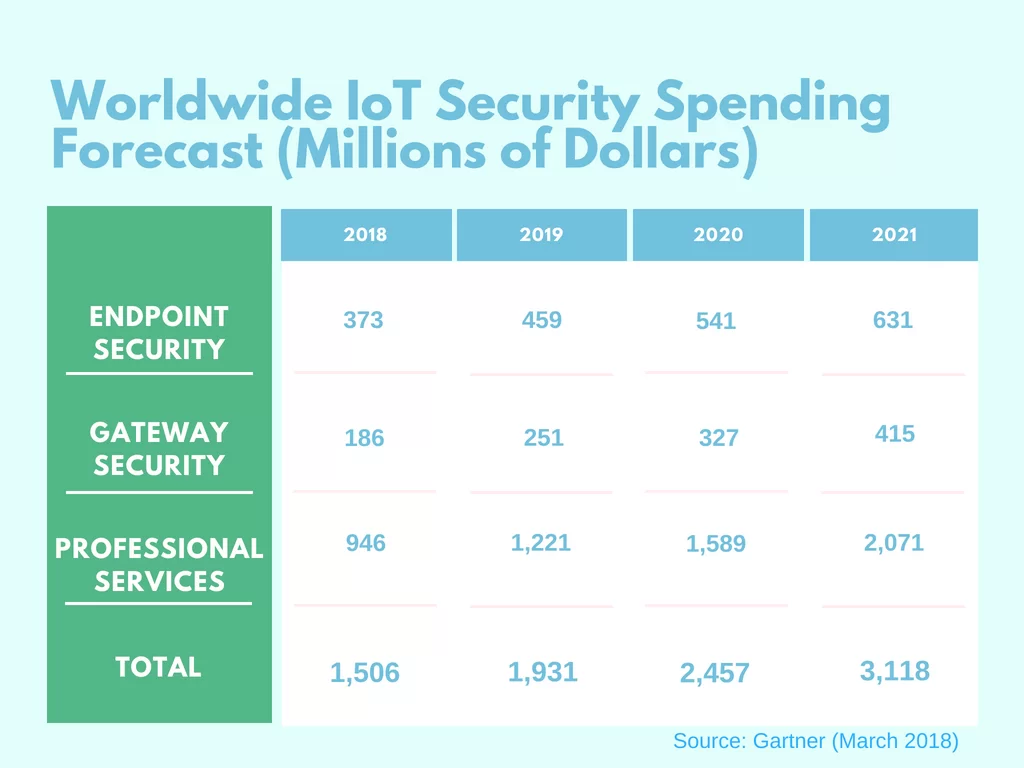
The important thing to know is that security is not just the responsibility of CIO’s, it is a common concern of top management, developers, users and even government. Regulatory compliance should become the top priority for the companies willing to innovate their businesses with IoT and improve critical infrastructure. That said, businesses are expected to spend more than $3.1 billion on IoT security, according to Gartner research.
With IoT concepts being implemented everywhere, from fitness trackers to Smart Factories, connected devices can be easily purchased and examined by hackers. That said, we should take in account that most of these devices are identical and have similar security settings which makes them more vulnerable to malicious attacks. Once a device is hacked, the producer should immediately counter the risks for other millions of the same devices and release updates as soon as possible. Otherwise, the sensitive data might be compromised which blows to the reputation of a manufacturer. That’s why the principle “forewarned is forearmed” should be an overriding principle for IoT device manufacturers, software developers and security officers.
Having recognized the security challenge, OWASP Foundation has initiated one of the most comprehensive IoT security guides having outlined top issues compromising IoT infrastructure:
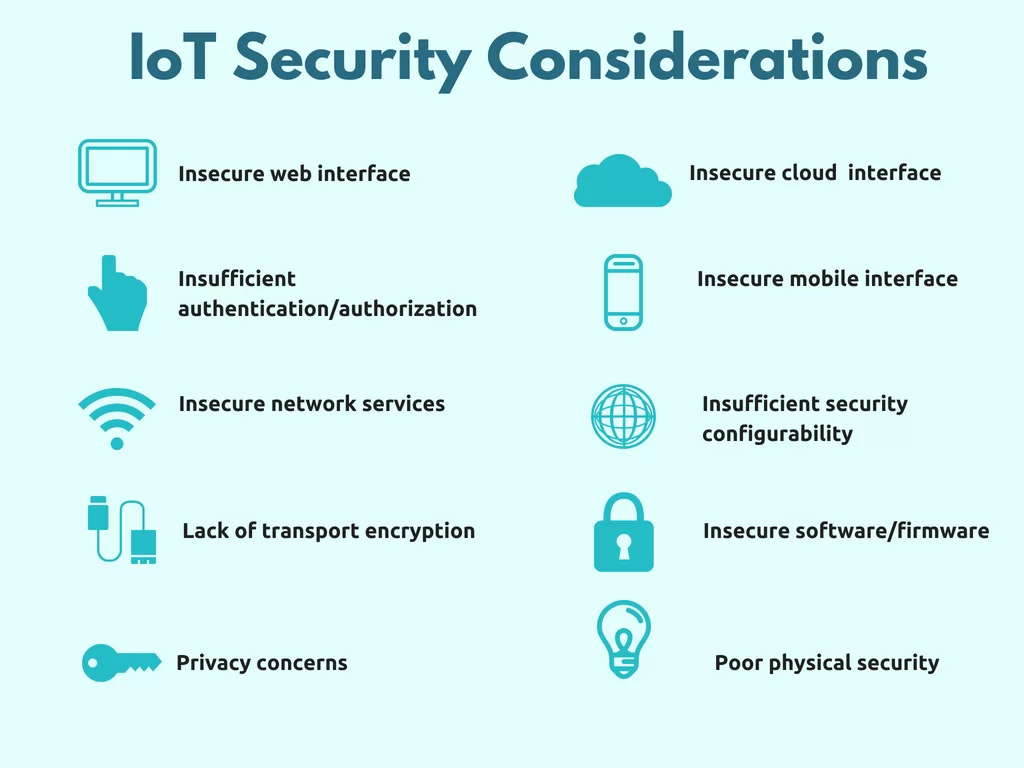
Here’s where a logical question arises: what should be done to overcome all the possible pitfalls on the way to secure IoT? It’s critical that all the entities in IoT infrastructure contribute to the protection of connected systems, from top management to users and third parties. Let’s see what issues should be addressed to lower risks and ensure data security.
Chief security officer’s take:
The earlier senior-level management gets onboard with security, the better organization they may provide. What are CSOs accountable for?
First, they should perform regular and all-embracing risk assessment and security audits to verify that no new devices and sensors are added without permission and no vulnerabilities are approaching.
Second, they should ensure staff awareness control. It’s critical to put onboarding processes in place to make sure that all developers, employees, partners and customers are familiar with the security processes and policies. The other challenge is to consider the fact that employees may bring BYOD devices which connect to the corporate network. This means they should be provided with the secure access to internal systems and
The other challenge is when someone is leaving the company and take a device with them. This implies the additional level of security and process layers within the organizational structure.
And remember: nothing is perfect. All networks and devices are subject to a certain level of vulnerability, so the emergency plan is a must. Every minute of unnoticed breach will cost your company lost money and unsatisfied customers.
Developers’ take:
What about IoT developers? They should care about the security from the very beginning of product development and put this priority over price and sometimes over the convenience of use.
Thus, developers should think over the mechanism for security that meets the needs of the connected devices and network considering memory issues, bandwidth availability and computing power.
Today, applications are often composed of libraries and components rather than developed from scratch, so the majority of risks can be eliminated by scanning these components for vulnerabilities. Even more, it’s better to employ proven and trustful technology stacks, encrypted channels and authenticated protocols (see the picture below):
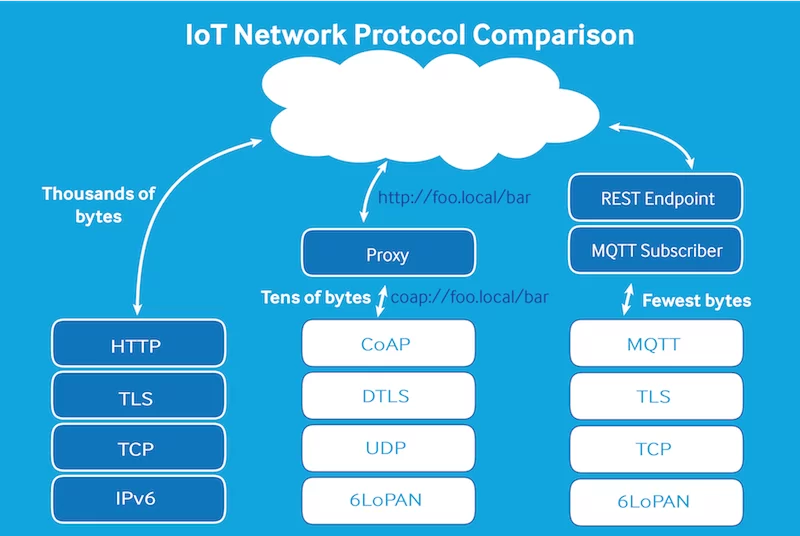
These security measures shouldn’t end up after being set up and run. The lion’s share of security concerns lies in continuous updates, upgrades and fixes of the whole system.
Also, it’s critical that developers protect users’ access to the system by providing them with two-factor authentication, request for default password change and password renewal over a certain period and timely system updates.
User’s take:
Although most of the security burden rests on the shoulders of the development team and chief security officers, users should care about their data as well. How exactly can customer contribute to IoT protection?
- Set strong passwords for IoT devices
- Store credentials securely, don’t share them over the network
- Accept any updates and upgrades of the system
- Not to browse the Internet on the devices which are not supposed for it
- Not to enter sensitive information
When buying IoT device, customers should mind security as a selection factor and make sure that only authorized users have access to data and networks.
In a nutshell:
The technology that powers the Internet of Things is developing, but so do the hacking attempts. The broad set of vulnerabilities associated with connected technology and the growing number of devices sold across the world require closer attention from CSO’s, developers’ and even users’ part.
That’s why for IoT manufacturers, as well as for companies willing to implement IoT strategy in their organization, hiring security experts is the indispensable part of risk management and meeting quality objectives.